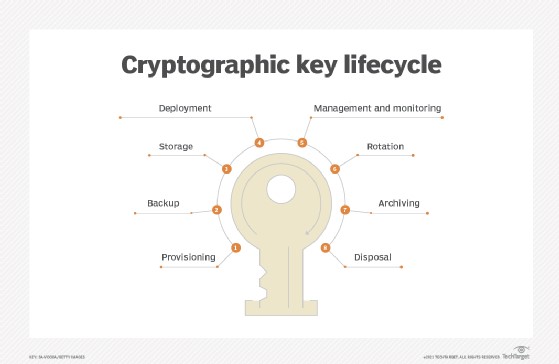
About Cryptographic Keys
Nowadays, people are searching for means of increasing and twice their hard-earned money. The method most frequently used for this is cryptography. Cryptography’s growing reliance also raises its susceptibility to hazards and threats.
Crypto networks contain a wide range of data, and it is unknown if this data is at risk. It may harm a community as well as an individual. Cryptographic keys keep the cryptography process functioning, but it is still important to keep them secure.
What exactly are Cryptographic Keys?
Cryptographic keys are widely used to solve cryptographic features, much like a regular key is used to access locks at homes. A string of data used to unlock or lock cryptographic operations is known as cryptographic key management. These processes include encryption, authorization, and authentication.
Cryptographic keys are also available in a variety of forms, sizes, and functions, just like physical keys do. These keys are divided into various groups based on the functions they carry out.
The Importance of Key Management
When protecting very valuable data, cryptographic keys must be carefully handled. Key management systems that are well-developed are frequently used to ensure that:
- Made to the desired length using a reliable source of random data
- Only by authorized staff who follow established standards
- Well-protected (usually using an HSM)
- Used only for the purposes for which they were mainly designed
- Deleted when not needed
- Updated as per their crypto-period
- Fully auditable to show proof of proper (or improper) usage
Common Functions for Cryptographic Keys
There are a variety of uses for cryptographic keys, some of which are described below. The related key’s characteristics such as length, type, and crypto-period, will be determined by the purpose for which it is used.
1. Authentication Key
Without a deep study of semantics, verification is frequently used in conjunction with symmetric encryption to provide assurance about the authenticity and/or creator of the related data. A quick and effective (HMAC) keyed-hash message authentication code approach that employs a symmetric key is often used to do this. The SHA-2 algorithm produces keys that are typically between 512 and 224 bits long, may be static or ephemeral, but typically have a short lifetime. AES-GCM, for example, supports modes in some encryption algorithms that offer authentication without the requirement for a different authentication key.
2. Data Encryption Key
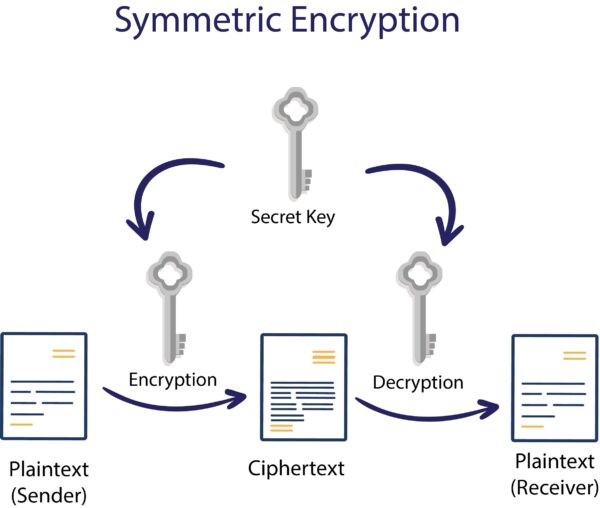
As was previously said, symmetric or asymmetric keys can be used to encrypt data to maintain its confidentiality. Key lengths for standard symmetric algorithms like AES and 3DES range from 256 to 128 bits, whereas those for typical asymmetric methods like RSA range from 1,024 to 4,096 bits. Asymmetric key-pairs normally have a longer lifespan of 1 to 5 years, whereas symmetric encryption keys can be either static or ephemeral with a crypto-period that is typically between a day and a year. If the material is to be maintained subsequent and encrypted access (i.e. decryption) is needed at a later time, keys may need to be kept longer than their crypto-period, or even eternally.
3. Digital Signature Key
Similar to authentication, digital signatures guarantee the authenticity and source of the associated data. However, they go a step further by incorporating the idea of non-repudiation, which prevents the signatory from erroneously asserting that the signature was faked. This calls for an asymmetric algorithm like ECDSA or RSA (key length: 1,024–4,096 bits) (key length 521-224 bits). The associated public key has an endless lifetime since it may be important to authenticate the sign at any time in the future, although the private key lifetime is often measured in years.
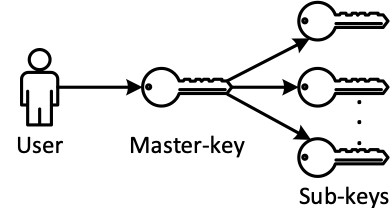
4. Master Key
A symmetric key known as a master key is employed to encrypt several inferior keys. Depending on the technique used, its length will normally range from 128 to 256 bits, and its lifespan may even be infinite. Therefore, it must be adequately safeguarded by installing an (HSM) Hardware Security Module.
5. Key Encryption Key (also known as Key Transport Key or Key Wrapping Key)
A secret key must be “wrapped” using an approved encryption process when it needs to be conveyed securely to maintain its confidentiality, integrity, and authenticity. Depending on the purpose, either asymmetric or symmetric encryption may be used. The length of the static, long-term key utilized for this encryption varies based on the technique being used and is designed to accommodate frequent modifications to the key that is being conveyed.
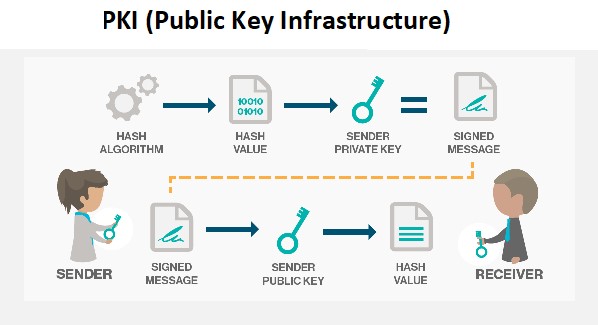
6. Root Key
The highest key in a (PKI) Public Key Infrastructure hierarchy, known as a root key, is used to sign and authenticate digital certificates. It is essentially an asymmetric key-pair, with a length that varies on the basis of the digital signature technique used, often between 256 and 4,096 bits. Such a key often lasts for a number of years, and a private key is frequently gained by an HSM.
Conclusion:
Symmetric and asymmetric cryptographic keys are the two basic types and depending on their intended use, they have different characteristics like the crypto-period and the length. Regardless of their characteristics and intended uses, all keys should be handled carefully throughout their lifetime to reduce the possibility of misuse (such as using a key incorrectly or for two separate purposes) or compromise.